Caffeine and Cybersecurity: Beware of TunnelVision's Sneaky Sip
Attention all coffee lovers and VPN users: there's a new threat brewing in the cyber world, and it's called "TunnelVision." Picture this: you're sipping your favorite brew at your local café, browsing securely with your VPN turned on, or so you think. Little did you know, hackers could be sneaking a peek at your unencrypted data while you're lost in the aroma of your coffee.
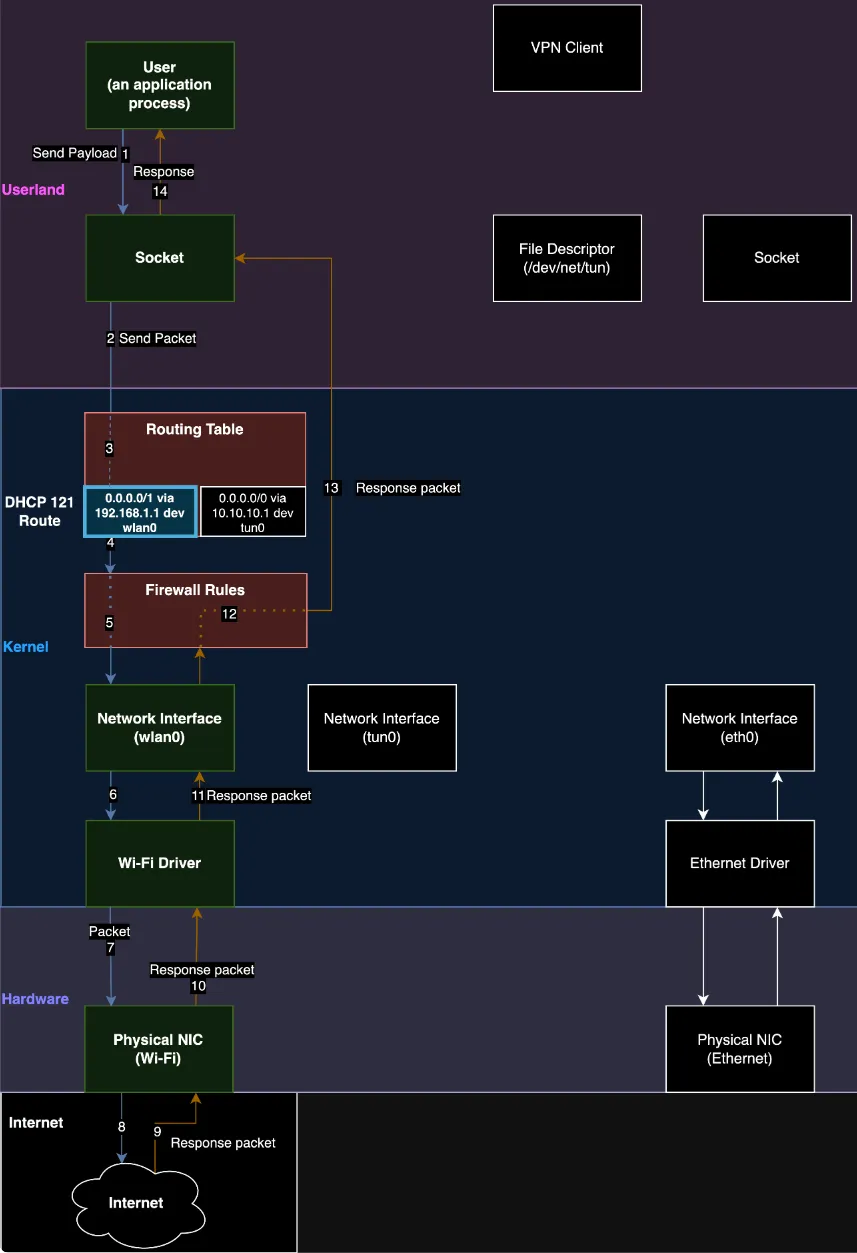
So, what's the deal with TunnelVision? Well, it's a clever trick that lets attackers sidestep the protective tunnel of your VPN, leaving your sensitive information vulnerable to prying eyes. This mischief relies on a sneaky maneuver involving something called Dynamic Host Configuration Protocol (DHCP) option 121. Basically, attackers play the role of a rogue DHCP server, manipulating your device's routing tables so that your VPN traffic skips the encrypted tunnel and lands straight into their waiting hands. Crafty, right?
But fear not, intrepid coffee drinkers of the digital realm! Leviathan Security has spilled the beans on this sneaky scheme, shining a light on the vulnerability (cue dramatic music) known as CVE-2024-3661. This flaw has been lurking in the shadows since at least 2002, but thankfully, there haven't been any reported cases of it wreaking havoc in the wild. Leviathan has rallied the troops, alerting affected vendors, as well as the cybersecurity guardians at CISA and the EFF, to tackle this brewing threat head-on.
Now, how can you safeguard your precious data from these devious cyber bandits? First off, be mindful of where you connect your devices. Public Wi-Fi hotspots, like those in coffee shops, hotels, or airports, are prime hunting grounds for TunnelVision attackers. And if your VPN client doesn't have anti-leak measures in place, well, you might as well be serving your data on a silver platter.
But wait, there's more! For TunnelVision to work its dark magic, you need to unwittingly connect to the rogue DHCP server before the legit one. Sneaky, right? Attackers have all sorts of tricks up their sleeves to increase their odds, from starving the legitimate DHCP server of resources to spoofing ARP addresses. It's like a game of cat and mouse, only with cyber crooks and unsuspecting coffee aficionados.
Now, onto the good stuff: mitigating the risk. Leviathan suggests a few caffeinated strategies:
- Linux Labyrinths: Dive into network namespaces on Linux to keep your routing tables safe from rogue DHCP configurations.
- VPN Vigilance: Configure your VPN client to block any traffic that doesn't go through the VPN interface. It's like setting up a security checkpoint for your data.
- DHCP Dexterity: Teach your system to turn a blind eye to DHCP option 121 while you're connected to your VPN. Sure, it might cause a hiccup in your connectivity, but better safe than sorry, right?
- Hotspot Hideaway: Consider cozying up to personal hotspots or nesting within virtual machines to shield yourself from DHCP shenanigans.
- Trust No Network: When in doubt, steer clear of untrusted networks, especially when you're handling sensitive info. It's like avoiding the shady alleyways of the internet.
And to all the VPN providers out there, take heed! It's high time to beef up your client software with some extra security measures. Whether it's crafting your own DHCP handlers or beefing up your defenses against risky configurations, every little bit helps in the battle against TunnelVision.
So, next time you're enjoying your cup of joe and browsing the web, keep an eye out for any suspicious sniffing around your VPN connection. After all, in the world of cybersecurity, it's better to stay alert than to spill the beans.




